Navigate Through the Storm with Proactive Exposure Management
Control Exposure and Maintain Visibility Across Your Entire Attack Surface With Exposure Management Solutions from DataFortified
Proactively identify and mitigate business risks with real-time insights
As your organisation’s digital footprint expand – from internal firewalls to the farthest reaches of the dark web – identifying and understanding your most significant vulnerabilities becomes increasingly complex. Determining which assets are most exposed, which third-party vendors pose the highest risk, and which threat activities are most relevant to your environment can be a daunting challenge.
DataFortified and our global partners provide comprehensive visibility into threats and exposures across your entire ecosystem, including your organisation, supply chain partners and the cybercriminal underground. With DataFortified, you gain actionable insights to proactively safeguard your digital infrastructure – whether on-premises, in the cloud, or throughout your extended supply chain.
Our Strategic Partnership Approach
Global Alliances
We’ve forged strong relationships with the world’s top security technology vendors, ensuring our clients benefit from the latest innovations in attack surface management.
Strategic Collaboration
By aligning with leading industry partners, we provide comprehensive visibility and control over your organisation’s digital footprint.

The Scale Of Our AI-Powered Intelligence Network
Our enriched intelligence delivers actionable insights into each threat’s characteristics and origins within seconds, enabling your security team to quickly understand and counter emerging risks.
7M +
7 Million Intelligence items curated each day.
540B +
Underground forums and marketplaces crawled.
1B +
Compromised credentials collected daily.
1 Min
Time taken from data collection to alerts being issued.
Our Core Risk Exposure Services

External Attack Surface Management
Uncover hidden assets, pinpoint and prioritise vulnerabilities, and view your digital infrastructure from an attacker’s perspective with External Attack Surface Management (EASM).
Impact-Based Prioritisation
Focus remediation efforts on vulnerabilities that pose the greatest real-world risk to your organisation.
Executive Ready Reporting
Leverage trusted metrics to produce clear, actionable reports that connect cyber exposure directly to business outcomes.

Continuous Monitoring
Supply chain attacks, zero day vulnerabilities and other cyber threats can emerge at any time – long before traditional annual assessments can detect them. Continuous Monitoring empowers your organisation to maintain real-time oversight of your vendor ecosystem and proactively address evolving risks.
Comprehensive Visibility
Monitor your entire extended attack surface, including third- and fourth-party vendors, to identify potential exposures as they arise.
Evidence Based Collaboration
Leverage objective, actionable data to work closely with your vendors and accelerate remediation efforts.
Effective Communication
Deliver critical third-party risk insights to stakeholders across the organisation, including executive leadership and the board, ensuring informed decision-making and stronger risk management.

Cyber Threat Intelligence
Empower your organisation to stay ahead of evolving threats with Cyber Threat Intelligence (CTI) that continuously captures, analyses and alerts your security teams to emerging risks, tactics, techniques, procedures (TTPs), and indicators of compromise (IOCs).
AI-Driven Insights
Receive enriched, actionable intelligence about the origin and nature of threats in under a minute, enabling rapid response.
Real-Time Threat Detection
Access up-to-the-minute findings on critical risk areas, including compromised credentials, vulnerabilities, ransomware, and active adversaries.
Customisable Alerts
Set tailored notifications for your highest-risk assets, ensuring your team is immediately informed of relevant exposures.
With advanced CTI, your organisation can identify, prioritise and mitigate risks before they impact your business.
Our platform collects over 7 million intelligence items daily from more than 1,000 underground forums and marketplaces, delivering unparalleled visibility into the threat landscape.

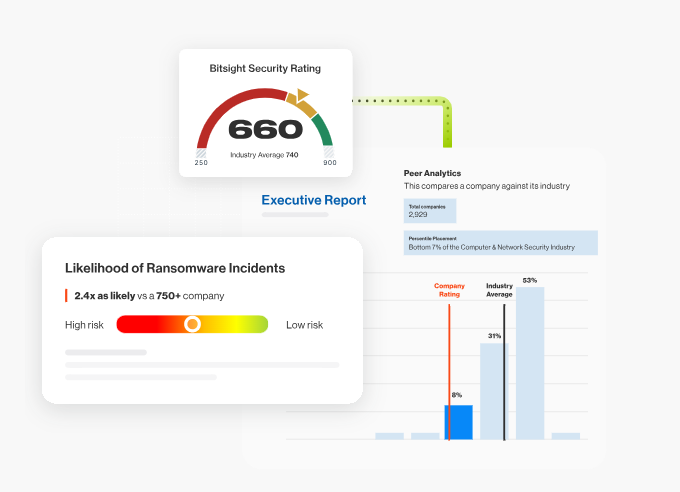
Security Performance Management
Leverage advanced analytics to eliminate uncertainty in evaluating your cybersecurity performance and setting programme goals. Metrics tailored to your organisation’s unique risk profile and security objectives provide actionable insights, enabling you to:
Benchmark
against relevant peer groups to understand your standing within your industry or sector.
Drill Down into Specifics
and areas of exposure, such as by hosting provider, subsidiary or asset inventory, for continuous digital improvement
Assess Effectiveness
of your security controls over the past six months, identifying trends and areas for improvement.
This data-driven approach ensures your cybersecurity programme is aligned with your business needs and risk tolerance, supporting informed decision-making and continuous improvement.
The Integrity and Accuracy of Strong Data is the Backbone of Efficient Cybersecurity
Our data is enriched with context to provide security teams with comprehensive insights into the nature and source of each threat in less than a minute following collection.
This rapid, contextualised intelligence allows your organization to make informed decisions and respond to threats with confidence. By understanding not just what the threat is, but who is behind it and how it operates, your security teams can prioritise risks, fine-tune defences, and proactively mitigate potential attacks before they escalate. With this level of visibility and speed, you can stay one step ahead of cybercriminals and safeguard your business against even the most sophisticated threats.
Get Your Free Advanced Cybersecurity Threat Scan and Report
Get ahead of the curve with an in-depth overview of your organisation’s security posture and any weak points within it. Claim your free, industry-leading cybersecurity threat scan and report today.
Enter your details below, click request and we'll do the rest!
We partner with the industry's leading providers of cybersecurity and threat intelligence globally - bringing you an unrivalled service and ensuring your business is in the know, ahead of the competition and protected at all times
Book a Free Expert Threat Intelligence Consultation
Submit the form below and a member our team will be with you shortly
Exposure Management F&Qs
What Is Exposure Management?
Exposure Management is a proactive approach to identifying and assessing cyber risks within an organisation’s digital environment. It helps prioritise vulnerabilities and improve security controls to reduce risk and strengthen overall cybersecurity.
What Is Exposure Risk Management?
Exposure in risk management refers to how much an organisation is at risk of loss or damage from specific threats. In cybersecurity, exposure encompasses all vulnerabilities and risks within an organisations digital environment – such as networks, applications, data and systems. By accurately assessing cyber exposure, organizations can gauge the effectiveness of their security measures and prioritise actions to address the most significant risks.
What Is Continuous Threat Exposure Management?
CTEM is a holistic security approach that empowers organisations to continuously identify, monitor, quantify and remediate threats across their entire attack surface – proactively staying ahead of potential attackers before vulnerabilities can be exploited.
What does the 'Exposure Factor' Mean?
EF in cybersecurity represents the percentage of an asset’s value that would be lost if a specific threat were realised. It estimates the impact of a successful attack on an asset. EF is often used to help calculate financial loss and inform risk management decisions.
What's the Difference Between Vulnerability Management and Exposure Management?
Vulnerability Management focuses on identifying, prioritising and fixing weaknesses in systems and software to reduce the attack surface. Exposure Management is broader, encompassing vulnerabilities, misconfigurations, assets and other risks to provide a complete view of an organisation’s exposure. It aims for proactive monitoring and mitigation of all potential attack vectors, not just known vulnerabilities.
We’re here to help
We’re in the business of reducing cybersecurity risk and safeguarding commercial businesses no matter their size or complexity. We understand our industry and subject matter can be confusing and that your time is precious, so we’ll do our very best to assist you effectively and present the best possible solutions for your specific needs. We look forward to hearing from you.